Now So I've been wanting to setup a domain controller on Microsoft Azure to ensure I always have a domain controller incase everything in my home lab blows up. I have not been able to do that until now because it requires a static IP address and I have had residential internet. Today I finally got my Buisness Class internet installed with static IP addresses so now I can do it.Supprisingly it was not that expensive with comcast! Lets see how it goes. First take a look at the environment I have to connect Azure to through Direct access:
TMG on Windows 2008 SP2 (still moarning the loss of TMG as a platform)
HP DL160 G4
8GB Ram
72GB SCSI HDD
Inside NIC
Outside NIC
My environment is a Windows 2012 R2 Hyper-V environment with System Center VMM and a 4GB Fiber Channel SAN (see Linux Fibre Channel SAN (Ubuntu)) With 8-15K SAS drives (0+1 raid array) for Hyper-V Storage.
My Hosts are a HP Proliant DL180 G6 with 61GB ram and a HP Proliant DL380 G5 with 32GB ram in a Hyper-V Cluster. I have had a Domain controller VM on each host stored on local storage in the event my SAN should go under, but thus far it has been reliable and has had very good performance.
First lets note TMG is not supported for Azure, but it is doable. There is a lot out there to guide you on it and credit goes where credit is do, I used the following 2 sites to help me accomplish it so credit should be given to them:
Windows Azure Virtual Network VPN with TMG 2010 by Marc Terblanche
- Log into Azure, go to Networks and create network:
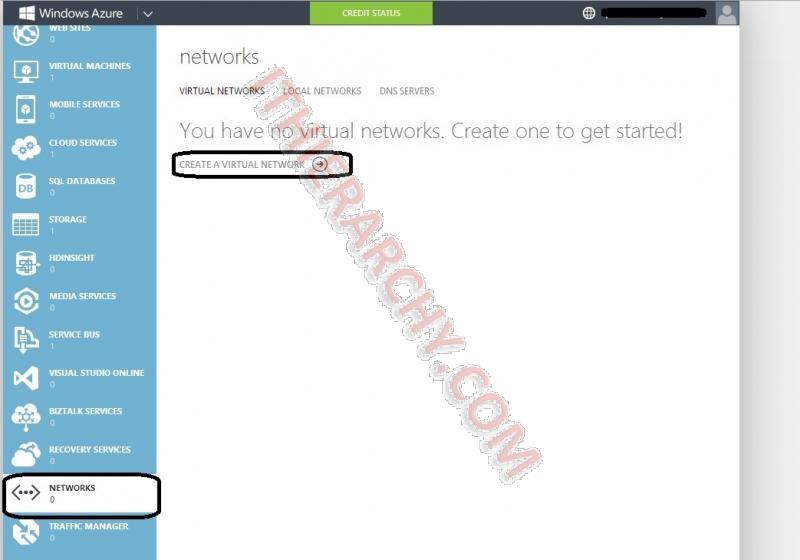
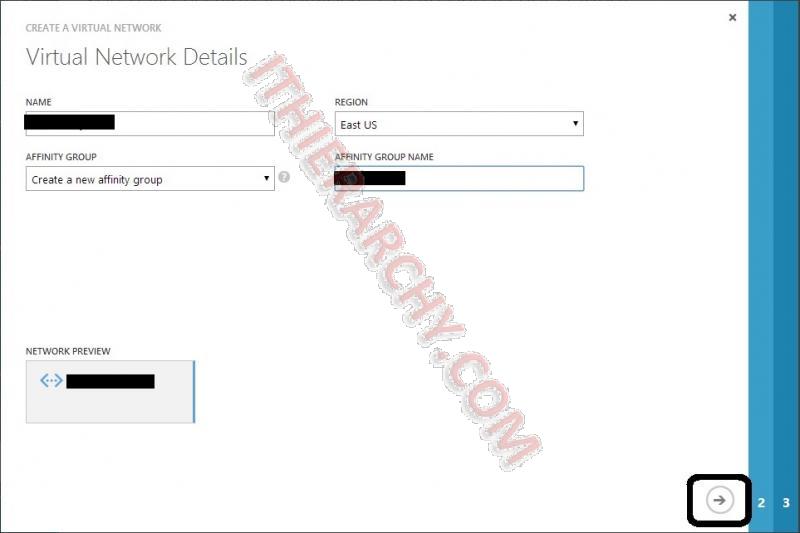
- Enter name and Select or create an Affinity Group. If you create an Affinity Group, you will need to create a name and specify a region. The Affinity Group, in short and way to simplistic, is a way to keep resources together and located at the same place. (see Importance of Windows Azure Affinity Groups for a good understanding of it)
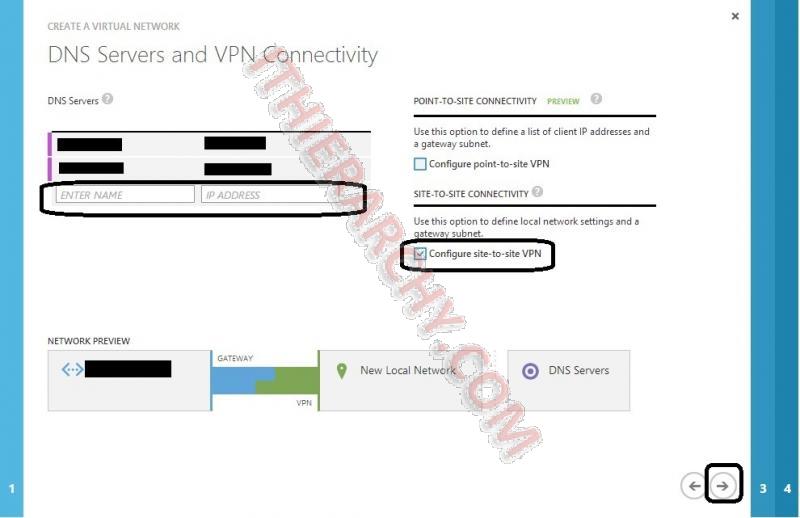
- Enter your internal DNS (DNS Servers You use for your local on premise network), Check "Configure site-to-site VPN"
- Site-to-Site Connectivity: This is important. Here you will enter a name for your VPN Network, Your PRIVATE IP space you use for your internal Network, enter a starting IP address,and the IP Count such as /24, /16, or what ever you use in your subnet mask for your internal network.
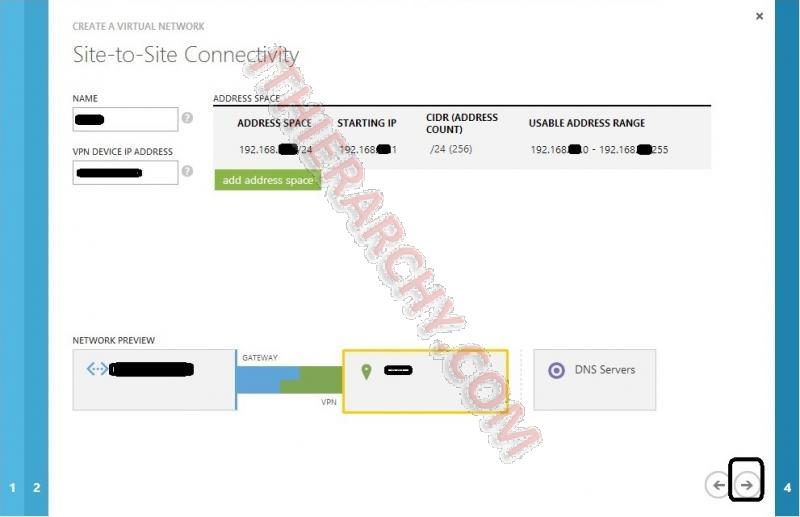
- Create your address space for your VPN. (different that above IP space). this will be the IP addresses that will be used in your Azure network.
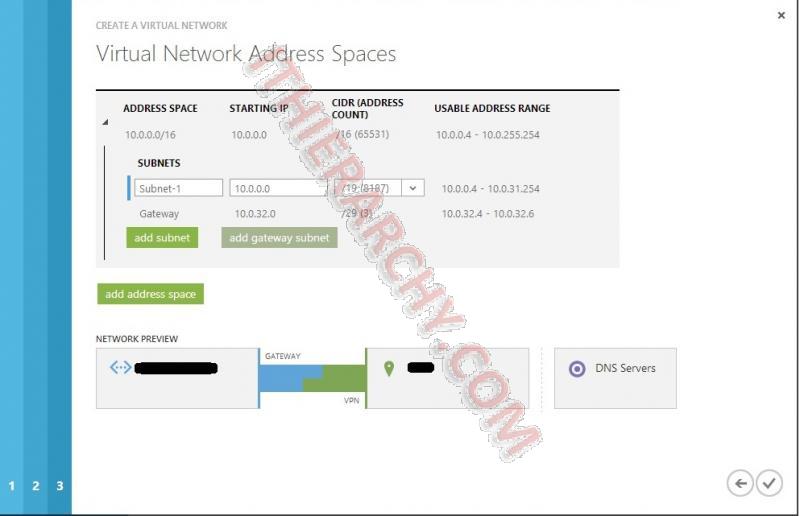
- Create Gateway: I choose static, but if you also want to do Point to site you will need it to be dynamic. it can take 15 minutes or so for the gateway to create. Take a break, get a cup of coffee, play with the kids...
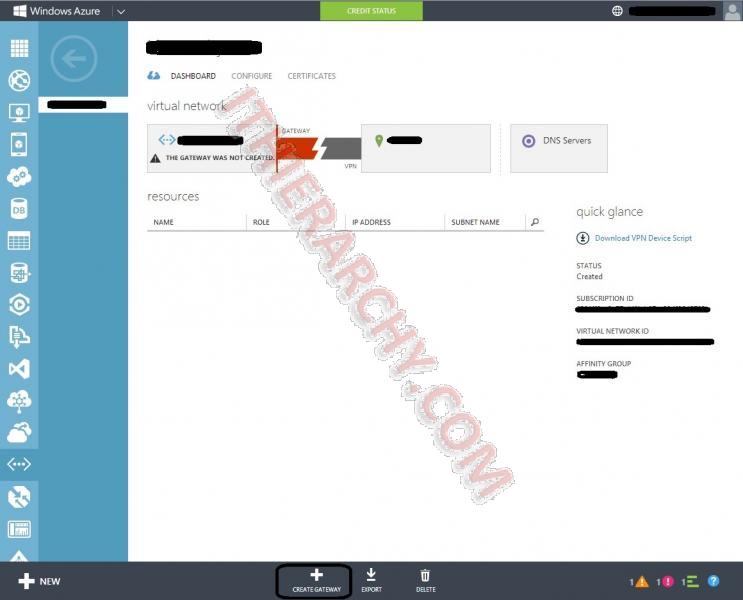
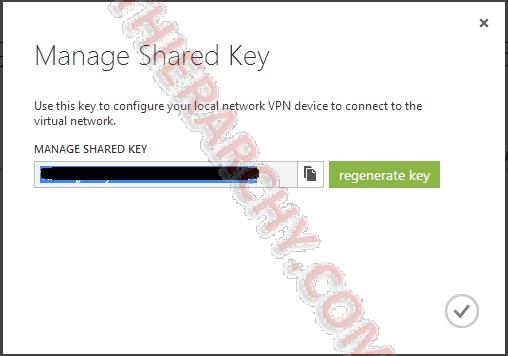
- Once your gateway is created, you need to make note of the Manage Key for step 10. Click Manage Key at the bottom:
Then make note (or copy and paste the key to notepad so you have it for step 10)
- Now we move on to the TMG server. On TMG you need to change the settings for your Perimeter Network. In the Forfromt TMG Console go to Networking and open the properties of the Perimeter Network. You will need to exclude the IP space your created in step 5 as well as the Gateway IP that came up in step 6. Say your internal address in 192.168.1.0/24 (192.168.1.1-192.168.1.254) and your Azure IP space is 10.0.0.0/16 (10.0.0.1-10.0.255.254), then you would need to set the following addresses for your TMG:
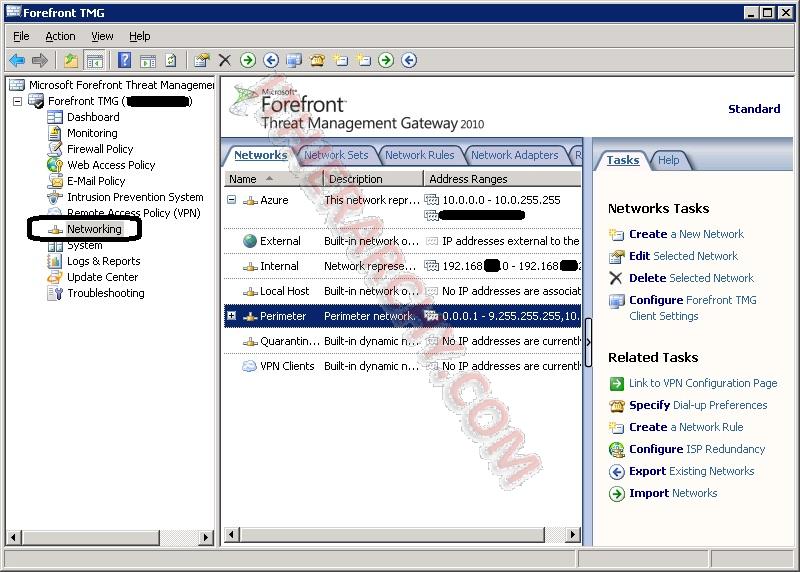
Start Address End Address Notes 0.0.0.1 9.255.255.255 10.1.0.0 126.255.255.255 128.0.0.0 137.23.12.11 End address one before Azure Gateway 137.23.12.13 192.168.0.255 Start address one After Azure Gateway 192.168.2.0 223.255.255.255 240.0.0.0 255.255.255.254 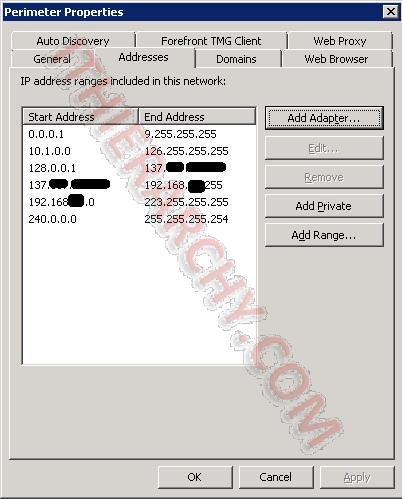
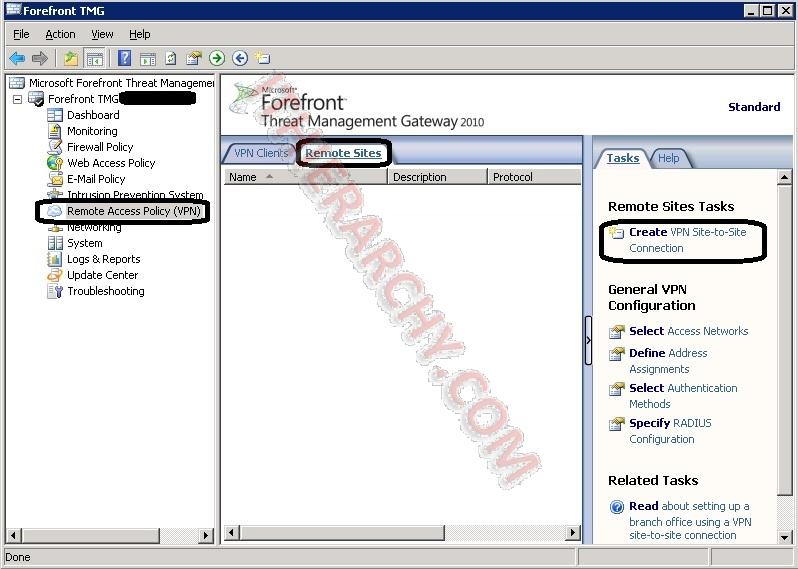
- Now we can create the Site-to-Site connection between Azure and TMG. Go to Remote Access Policy (VPN), select Remote Sites. Click the "Create VPN Site-to-Site Connection"
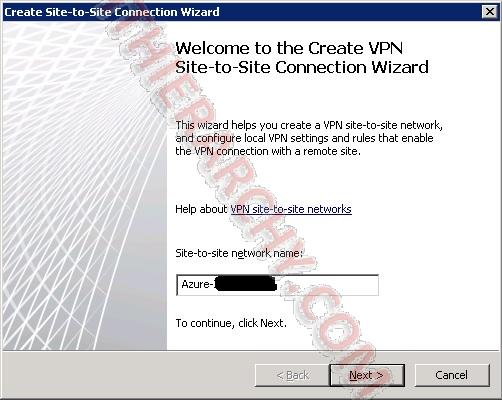
- Now we will go through the Wizard for Create Site-to-Site Connection. We need to give it a name:
Select IP Security protocol (IPsec) tunnel mode
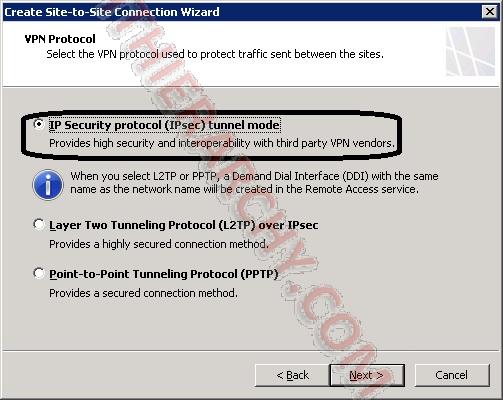
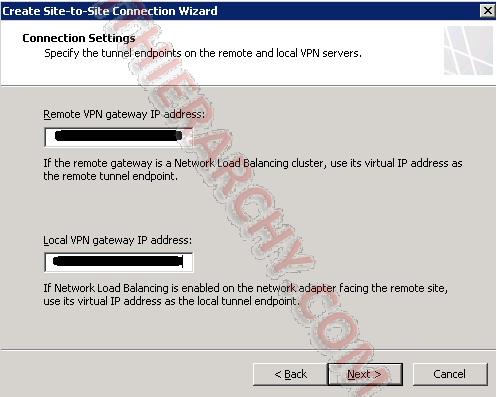
Noew you need to enter the 2 Public IP address for the 2 sites. In the First box (Remote VPN gateway IP address), enter the Gateway address from step 6 for the Azure Site. In the second box (Local VPN gateway IP address), enter the Public IP address provided to you by your ISP that your TMG server is connected to. This IP address needs to be connected directly to your TMG server, no NAT.
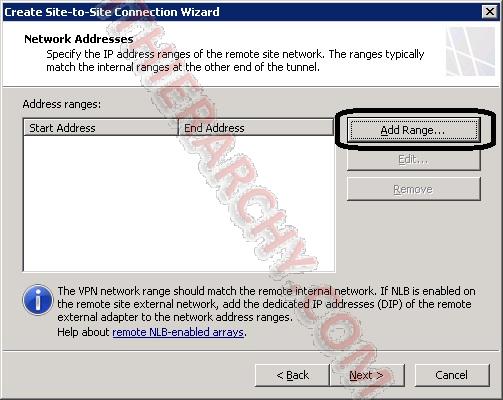
You will need to add the range of your Azure network and the Gateway IP address (from step 6) for the Azure Network:

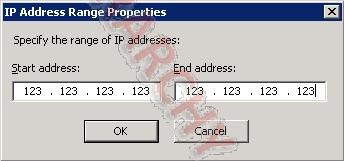
Example of adding the Azure Gateway IP:
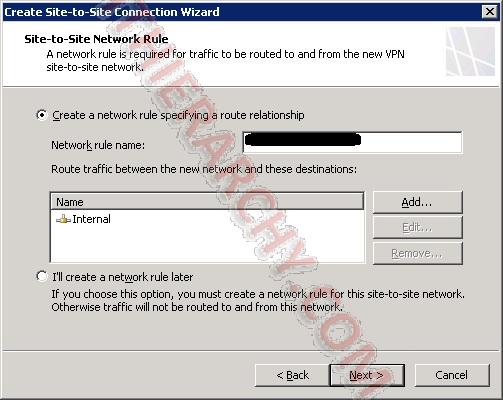
Next the wizard will ask if you want to create the Network Rule for internal to Azure site. let it create the rule.
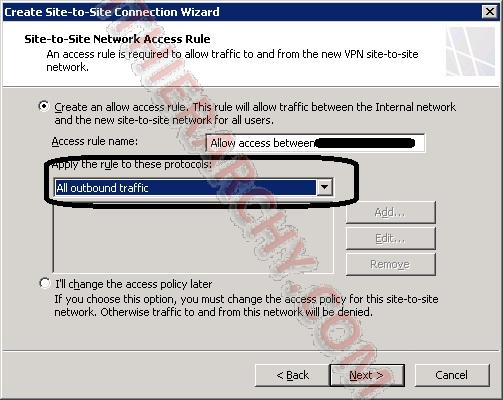
Now it will want to create a access rule for the Firewall. You will want it to "Ally the rule to these protocols: "All outbound traffic":
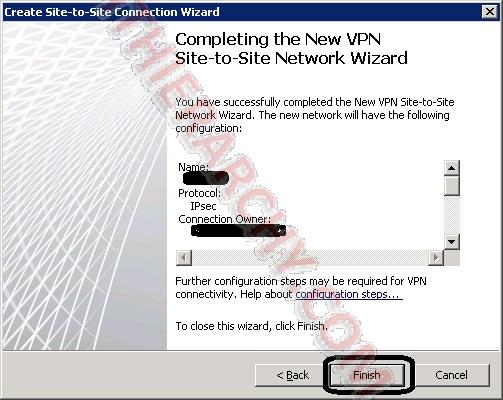
Now finish the wizard:
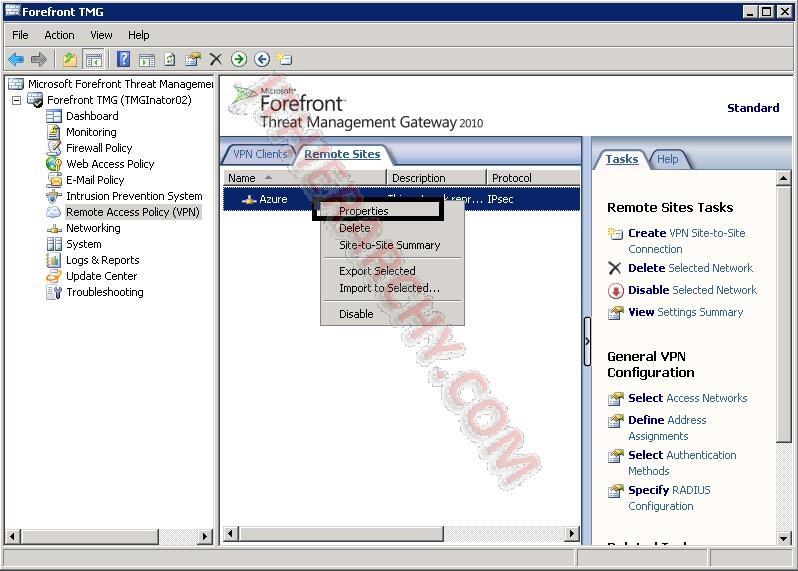
- We are almost there, but we still need to make some tweaks to the remote site, so go back to the Remote Access Policy (VPN), right click on the Azure Site and select Properties.
Select the Connection tab, then click the "IPsec Settings..." button.
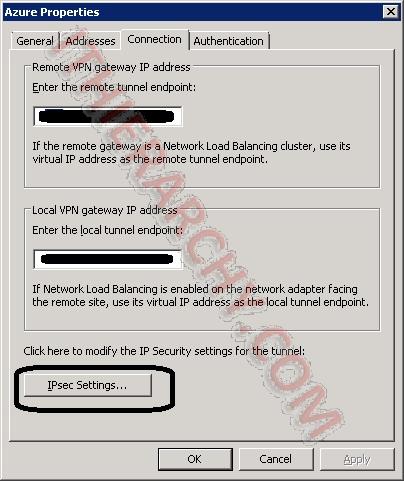
On the Phase I tab, set the Following:
Encryption algorithm: AES128
Integrity algorithm: SHA1
Diffie-Hellman group: Group2 (1024 bit)
Authenticate and generate a new key every: 28800 seconds
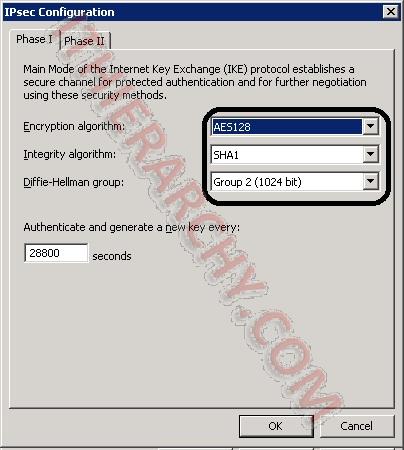
On the Phase II tab make sure the following is set:
Encryption algorithm: AES128
Integrity algorithm: SHA1
Diffie-Hellman group: Group2 (1024 bit)
Check the "Generate a new key every:" box and set to 102400000 Kbytes
Check the "Generate a new key every:" box and set to 3600 seconds
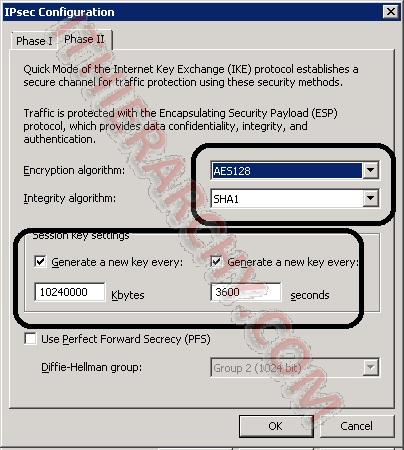
Now to be on the safe side and since you are there anyhow, double check the Authentication tab and ensure the pre-share key for authentication you created in step 7 is entered:

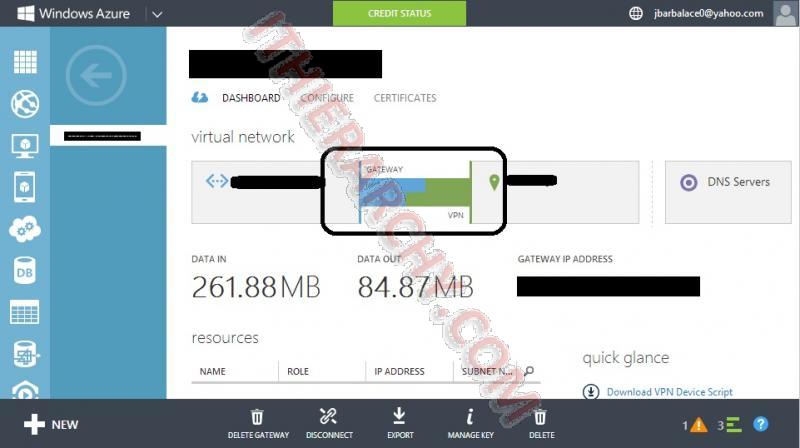
- Now if you go back to the Azure Portal you should see it connected. if it is not, you can click connect, wait a minute or to and it should connect!
- Others have said you need to set MTU to 1350 on external network adapter, I have tested it both ways, and it now works on Azure set at the default 1500, and my network gets better performance on the 1500 MTU setting. If you find you are having issues, you might try setting the MTU down to 1350 by running the following lines:
netsh interface ipv4 set subinterface "External" mtu=1350
verify with:
netsh int ip show int

Comments